How
well are you protected on the internet?
Check how many myths you believe in ...
Internet
has not only made it easy to network with your friends and
families, but it has also made it easier for the harmful
elements to intrude into your private life.
In
earlier years, you were infected with spywares which corrupted
your files and made your system non-functional. But today's
malwares like Scareware, Ransomware and Identity theft bots
are much advanced and can cause havoc to your day to day
life. The Scareware (which really scares
you) makes you believe that you are infected with virus
and you have to clean it immediately with the software ready
to be downloaded. Once downloaded, you are at their mercy.
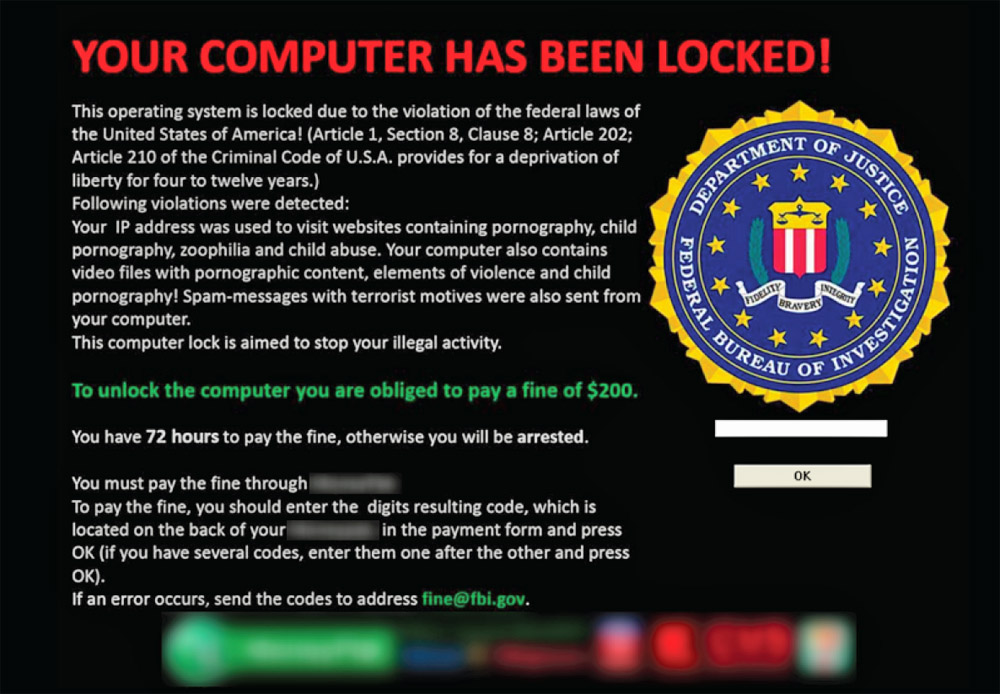
On the other hand, Ransomware (which really
wants a ransom from you) makes you believe that you have
broken a Government law and you need to pay a penalty within
72 hours or face a jail term. The penalty can be anywhere
from $200 and upwards and has to be paid online immediately.
Identify theft bots (automated programs)
are not that scary like Scareware or Ransomware. But it
resides stealthily on your computer waiting for you to disclose
your bank pin or debit/credit card details. Once it captures
the data it sends it to the Identify thieves network who
use this data to withdraw your money or shop away with your
credit card information at remote locations.
Now,
how well are you protected against these threats on the
internet? Do you believe in the following myths?
Time
to know it!
Also,
get familiarized with some of the Scareware
pop-up images and Ransomware
pop-up images you may encounter if you are attacked.
|
|
|
"There is nothing on my computer
which any one would want."
a. Yes, I believe this.
b. No, I don't believe this.
c. I don't have a strong opinion on this.
Answer: [b]
Don't think there is always a human behind a hacking.
Internet is infested with millions of automated programs
(also known as bots) which polls (looks) for vulnerable
systems on the network. Studies have reported that it takes
just 7 minutes for a new unprotected computer installed
on internet to get compromised. So, your unprotected computer
gets compromised whether you have important information
or not! With more and more business transactions occurring
over web (like web store, online tickets, bank payments)
you are worth more than what you think!
There are tools available on internet
to find your black market value and insurance available
to protect you from any identity breach. Take a look!
|
|
|
"It is very easy to know whether
my computer has an infection; It will become slow and behave
strangely. Moreover I have a free anti-virus software on
my machine which can protect my computer"
a. Yes, I believe this.
b. No, I don't believe this.
c. I don't have a strong opinion on this.
Answer: [b]
Sorry, the infection techniques have evolved further.
Today's malware (bad software) can stay dormant on your
system for months or years before attacking you. For example,
you can be infected with a keylogging malware (a software
which can capture your keystrokes) which can stay dormant
until you type your bank pin or you make a credit card purchase.
All this thing can occur in the background without any noticeable
impact to the performance (without taking CPU cycles).
There are 2 types of anti-virus softwares.
One that protects you real time (when the attack is occurring)
and One that helps to clean after the attack. It is preferable
to get the first one as it saves lot of time cleaning. Check
which family of free software you have. Additionally, your
free anti-virus software may or may not be up to date with
all virus signatures. So relying on free anti-virus software
can make you vulnerable to malware attack. Believe us, this
information is not provided to support any anti-virus software
vendors but to educate you about the threat around you.
|
|
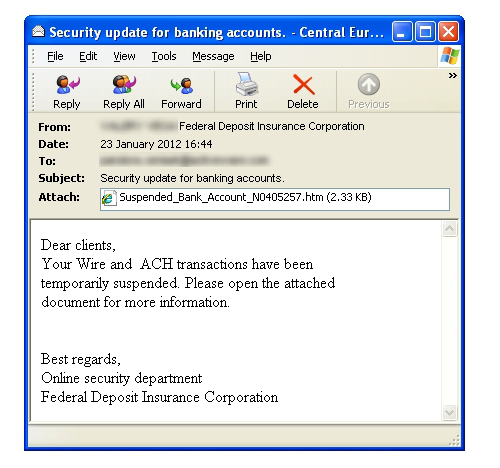
"Malware comes from email
attachment. If I don't open the attachment I am completely
safe. Also, any link posted by my friends on social
network (Facebook, Twitter) is safe."
Malware: Computer
Virus, Worms, Trojan Horses and other software which
are harmful to your system.
a. Yes, I believe this.
b. No, I don't believe this.
c. I don't have a strong opinion on this.
Answer: [a, b]
Even though the technique of sending malwares through
attachment still exists, it is not your only threat.
Today's threats come through URLs, Facebook links, Twitter
links under your friends name. The simple technique
is do not open an attachment or click on an URL unless
you are sure about the orginiator. If you want to really
check the safety of the URL, you can use this tool
provided by Symantec.
Additionally, be informed that the
malware problems are not extending into your smart phone,
tablets and other hand held gadget world. It is now
very important to be aware of other "nodes of vulnerability".
|
|
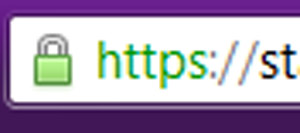
"If my browser displays a locked
padlock then the web site is safe."
a. Yes, I believe this.
b. No, I don't believe this.
c. I don't have a strong opinion on this.
Answer: [a, b]
This is the impression every one had until the heartbleed
defect came to limelight. This highlighted the false security
we are faced in this internet world. Always keep in mind
that you are vulnerable to sniffing unless you are connected
through a peer-to-peer, dedicated and encrypted connection.
|
|
"My firewall can protect my system
from drive-by attacks such as Scareware, Ransomware, Trojan
Horses, Viruses and Worms."
a. Yes, I believe this.
b. No, I don't believe this.
c. I don't have a strong opinion on this.
Answer: [b]
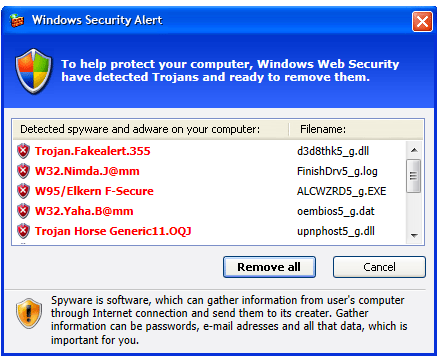
Unfortunately, at this point, your firewalls are not
fool-proofed to identify "drive-by" attacks which
poses a regular traffic. This exposes you to Scareware (A
malware which warns repeatedly that your computer is infected
even though it is not infected), Ransomware (A malware which
will not allow you to login to your computer until you call
a number to pay to clean up), Trojan Horses (A malware which
disguises behind a valid software), Viruses and Worms.
Bottomline, don't fall prey to common
computer myths!
|
|
|
Bottomline,
Don't fall prey for common computer myths! |
|
|